Note: The first part of this page applies to SiteRemote 6.2 and higher and SiteKiosk Online. For older versions please see the second part of this page.
SiteRemote Server 6.2 and higher and SiteKiosk Online include an LDAP configuration option on the Settings page of the SiteRemote/SiteKiosk Online server. SiteRemote/SiteKiosk Online support the LDAPv3 protocol, please make sure that your LDAP server supports this protocol version.
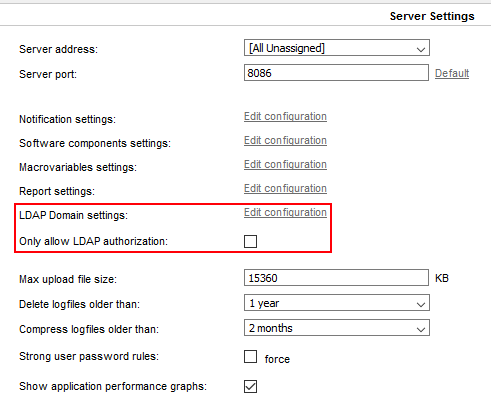
Click on Edit configuration to create a set of LDAP settings. If you only want LDAP authorization to be allowed on your SiteRemote/SiteKiosk Online server use the Only allow LDAP authorization checkbox, login with local SiteRemote users will then be deactivated.
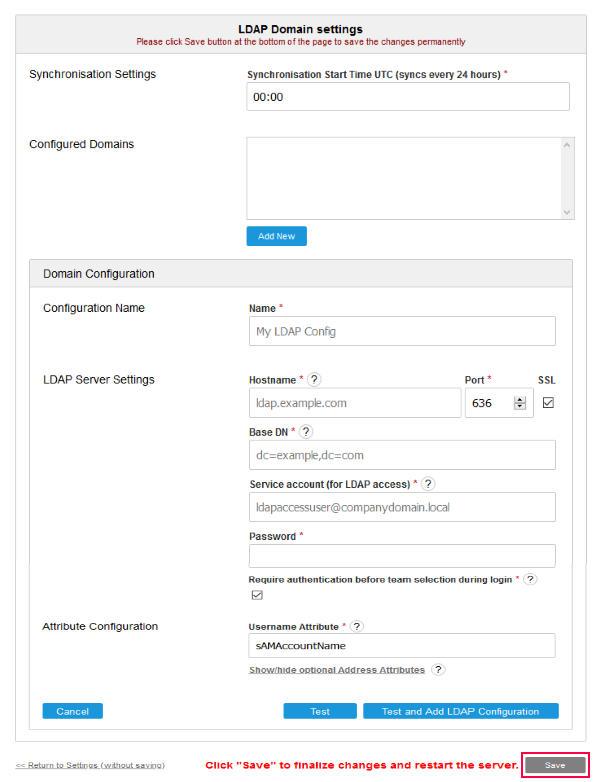
On the configuration page you can set the time for the daily LDAP synchronization. You can also add as many LDAP domains as you want, e.g. to assign different LDAP servers to your SiteRemote/SiteKiosk Online teams. You can edit or delete existing domains, note that you cannot delete a domain if it is assigned to a team. Click on Add New to add a domain configuration. Choose a name for your LDAP domain configuration and make the settings according to your LDAP environment. Use the help icons (?) for additional information for each setting. Click on the Test button to test your settings and click on the Test and Add LDAP Configuration button to test and save your LDAP configuration.
IMPORTANT: Once you are done with creating or editing the LDAP settings, click on the Save button (marked in red on the screenshot above) to fully save and activate your LDAP settings. The SiteRemote/SiteKiosk Online server will be restarted for that purpose.
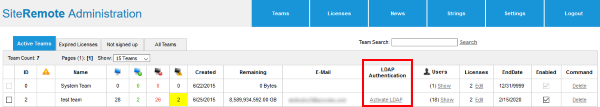
Next go to the Teams page of the SiteRemote/SiteKiosk Online administration and create a team or choose an existing team. Please note that you first need to create a team before you can assign the LDAP settings to it. Click on Activate LDAP to assign LDAP authentication to a team or Modify/Deactivate LDAP to change or remove LDAP settings from a team.
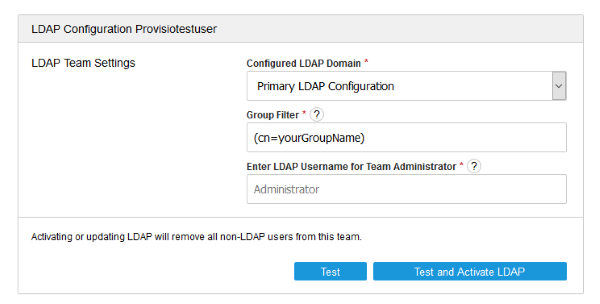
Choose an existing LDAP domain from the dropdown and assign one or more groups from your LDAP server. Choose one LDAP user that is part of a selected LDAP group to be the administrator of the SiteRemote/SiteKiosk Online team. Use the help icons (?) for additional information for each setting. Use the Test button to test your settings and the Test and Activate LDAP button to test and assign the LDAP settings. All local SiteRemote/SiteKiosk Online users will be removed from a team once LDAP is activated, the same applies to all LDAP users when disabling LDAP for a team. Login with the LDAP user that has been assigned as the team administrator to set the SiteRemote/SiteKiosk Online team rights for the other LDAP groups and users that have been assigned to the team.
Please note that the user name you need to use when registering or unregistering a client is ldapusername+siteremoteteamname, e.g. miller+yourcompteam (Note: this is not necessary when using the preconfigured SiteKiosk Online Windows client installer). SiteRemote/SiteKiosk Online maps the LDAP user to an internal user. Because you can assign the same LDAP user to different teams, the teamname is added with a plus sign to create the internal user name. This only applies to registering or unregistering a client, the SiteRemote/SiteKiosk Online login page will show a team selection drop down field if required to handle the LDAP login of the same user to different teams.
Please note that the SiteRemote Server needs to trust the LDAP server when using SSL for the connection, if you are using self-signed certifcates you may need to import your root certificate as a trusted certificate authority into the Windows certificate store.
Also note that the AutoRegister tool of SiteRemote does not support LDAP users due to technical limitations. The AutoRegister tool of SiteKiosk Online (and also the preconfigured Windows client installer) can be used in LDAP environments.
Note: The following applies to the release version 5.1.0.2188 up to 6.1. For compatibility reasons with OpenLDAP the syntax of the user.config section has been changed from the original release version 5.1.0.2186. The old syntax is no longer supported.
With SiteRemote Server 5.1 we introduced LDAP user mapping for customers running their own SiteRemote server. Now you can use user credentials provided by the directory service of your company's domain (q.v. Active Directory) for authentication in SiteRemote.
LDAP users and normal SiteRemote team users can be used together. At least one SiteRemote team user is required for each team you want to map LDAP users to.
Before you can map LDAP users to SiteRemote you need to create at least one team. You can do that for example on the Teams tab of the SiteRemote Server Administration. Note that while creating the team you need to specify a user, this user must not be an LDAP user but a normal SiteRemote Team user. This is the user responsible for a team and it cannot be deleted when logged in with an LDAP user. You can only delete this user from another SiteRemote team user account within a team (Note: it is planned for future SiteRemote versions to make the primary administration user permanent, so this behaviour might change).
After the team creation you can proceed to prepare your SiteRemote server to use LDAP authentication. You now need to manually edit the configuration file of the server. You will find the SiteRemoteServer.config file under ..\PROVISIO\SiteRemote\Config. Open it with an editor like Notepad and scroll down to the bottom. There you need to change the default User.config section right before the closing configuration tag:
<User.config LdapServerPort="0" LdapSecureSocketLayer="false" />
to something like this:
<?xml version="1.0" encoding="utf-8"?>
<Configuration>
...
...
<SiteCaster.config VideoAudioAnalyzerPath="VideoAudioAnalyzer.exe" />
<User.config>
<LdapImportFullFilePath>c:\ldapuserlist.csv</LdapImportFullFilePath>
<LdapServerHost>ldapserver.yourdomain.biz</LdapServerHost>
<LdapServerPort>389</LdapServerPort>
<LdapSecureSocketLayer>false</LdapSecureSocketLayer>
<LdapUserPatterns>yourcompany\{0}</LdapUserPatterns>
</User.config>
</Configuration>
The User.config section is the parent element for all LDAP related child elements in the SiteRemote configuration.
The LdapImportFullFilePath element must include the full path to the .csv file that includes the domain users you want to map to SiteRemote. More on that file a little later.
LdapServerHost includes the full host name of your LDAP server, you may also use an IP adress.
LdapServerPort specifies the port your LDAP server uses. The default LDAP port is 389 or 636 if using an SSL connection.
LdapSecureSocketLayer is a boolean value. It is true if the server uses SSL.
LdapUserPatterns defines the way SiteRemote queries the user with the LDAP server. There are three supported principal forms: LDAP DN, Kerberos and NTLM. Note that these forms cannot be mixed. {0} is a required part of the pattern and is replaced by SiteRemote to include the user name that is authenticated with the LDAP server. The same user data is also used to perform the LDAP request.
LDAP DN uses the LDAP distinguished name syntax. This is used for example in OpenLDAP installations like Novell eDirectory.
<LdapUserPatterns>cn={0},ou=users,ou=us,o=yourcompany</LdapUserPatterns>
Because that syntax is very specific in regards to the location that is queried within the LDAP structure, you can add more than one pattern. The patterns must be seperated by a semicolon.
<LdapUserPatterns>cn={0},ou=users,ou=california,ou=us,o=yourcompany;cn={0},ou=users,ou=de,o=yourcompany;cn={0},ou=users,ou=gb,o=yourcompany;</LdapUserPatterns>
Kerberos authentication is usually used in Windows Active Directory. This syntax does not require different patterns as it queries the complete LDAP tree.
<LdapUserPatterns>{0}@yourcompany.biz</LdapUserPatterns>
NTLM authentication is also commonly used in Windows Active Directory. This syntax does not require different patterns as it queries the complete LDAP tree.
<LdapUserPatterns>yourcompany\{0}</LdapUserPatterns>
Here is another full example that uses SSL and LDAP DN:
<?xml version="1.0" encoding="utf-8"?>
<Configuration>
...
...
<SiteCaster.config VideoAudioAnalyzerPath="VideoAudioAnalyzer.exe" />
<User.config>
<LdapImportFullFilePath>c:\ldapuserlist.csv</LdapImportFullFilePath>
<LdapServerHost>ldapserver.yourdomain.biz</LdapServerHost>
<LdapServerPort>636</LdapServerPort>
<LdapSecureSocketLayer>true</LdapSecureSocketLayer>
<LdapUserPatterns>cn={0},ou=users,ou=california,ou=us,o=yourcompany;cn={0},ou=users,ou=de,o=yourcompany</LdapUserPatterns>
</User.config>
</Configuration>
After making and saving the changes to the SiteRemoteServer.config file you need to restart the SiteRemote Server service in the Microsoft Management Console for Windows Services (services.msc).
Now its time to create and place the .csv file with your LDAP user list at the location you specified in the SiteRemote configuration file. Note that the file only needs to contain the LDAP users you actually want to use with SiteRemote and not all LDAP users in your domain. Each line of the .csv file represents one LDAP user. The syntax is as follows:
[<oldusername>],<username>,<team>,<role(s)>,[<group(s)>]
oldusername is optional and required if you want to rename a user and keep this user's assignments within a SiteRemote team. This can be useful due to a name change because of marriage for example. oldusername then specifies the existing name of the user and username would contain the new one. Providing a name in this field is optional, if you don't provide a name you still need to write the comma to separate this field from the next. Note that user names must be unique, each user name can only be used once.
username specifies the name of the user. This field is required. Note that user names must be unique, each user name can only be used once.
team specifies the SiteRemote team name you want to assign the user to. This field is required.
role(s) (optional since SiteRemote Server 5.2 or higher) specifies the role or roles that you want to assign to the user. The role names of the default roles are language specific and depend on the language that was assigned at the time the team was created. For example the default roles for English are Administrator, User and Guest, in German they are Administrator, Benutzer and Gast. Other roles can be created and individually named in a SiteRemote team under Administration -> User Roles. If you want to assign more than one role you need to use quotation marks and separate each role by a comma.
group(s) is optional and only available with SiteRemote Server 5.2 or higher. You can assign LDAP users to groups you have created. If you want to assign more than one group you need to use quotation marks and separate each group by a comma. Note that each user will be automatically assigned to the Everyone group of a SiteRemote team.
Generally quotation marks are recommended to be used for each field. Here is an example of how the file can look like:
,"LDAPuser1","team1","Administrator"
,"LDAPuser2","team1","Guest"
,"LDAPuser3","team2","Administrator"
,"LDAPuser4","team2","User,Team2Role1,Team2Role2"
"LDAPuser5","LDAPuser7","team2","Guest"
,"LDAPuser6","team3","Administrator","Admin Group"
Note that the empty lines between the teams are not required, yet they can be used to better visualize assignments for different teams.
Each time you edit and save the .csv file or overwrite the existing file with a new one, the changes are applied.
To remove a user, simply delete the line from the .csv file and save it. The following would remove LDAPuser4 from team2:
,"LDAPuser1","team1","Administrator"
,"LDAPuser2","team1","Guest"
,"LDAPuser3","team2","Administrator"
,"LDAPuser7","team2","Guest"
,"LDAPuser6","team3","Administrator","Admin Group"
To remove all LDAP users from a team, just remove them all from the file. Placing an empty file will remove all LDAP users from all teams. The next example will remove all LDAP users from team2:
,"LDAPuser1","team1","Administrator"
,"LDAPuser2","team1","Guest"
,"LDAPuser6","team3","Administrator","Admin Group"
In case you want to assign a group but no role, the line would look like this:
,"LDAPuser6","team3",,"Admin Group"
Status messages regarding the processing of the file can be found in the SiteRemote server log file. The file SiteRemote.log can be found under ..\PROVISIO\SiteRemote\Log.
For full functionality the LDAP user authentication requires SiteKiosk Android 2.2 or higher or SiteKiosk Windows 8.9 or higher. Older versions cannot be registered with the SiteRemote server using an LDAP user.
In case you are using the TerminalCommander tool please make sure you are using the version that comes with SiteRemote Server 5.1 or higher.
Please note that the AutoRegister tool of SiteRemote does not support LDAP users due to technical limitations. The AutoRegister tool of SiteKiosk Online (and also the preconfigured Windows client installer) can be used in LDAP environments.